Authors: Jonathan Evans and Neha Sahgal
 Sikh devotees light candles at the Golden Temple in Amritsar, India, on June 25, 2021. (Narinder Nanu/AFP via Getty Images)
Sikh devotees light candles at the Golden Temple in Amritsar, India, on June 25, 2021. (Narinder Nanu/AFP via Getty Images)
India’s massive population is diverse as well as devout. Not only do most of the world’s Hindus, Jains and Sikhs live in India, but it also is home to one of the world’s largest Muslim populations and to millions of Christians and Buddhists.
A new Pew Research Center report, based on a face-to-face survey of 29,999 Indian adults fielded between late 2019 and early 2020 – before the COVID-19 pandemic – takes a closer look at religious identity, nationalism and tolerance in Indian society. The survey was conducted by local interviewers in 17 languages and covered nearly all of India’s states and union territories. Here are key findings from the report.
How we did this
1. Indians value religious tolerance, though they also live religiously segregated lives.
Across the country, most people (84%) say that to be “truly Indian,” it is very important to respect all religions. Indians also are united in the view that respecting other religions is a very important part of what it means to be a member of their own religious community (80%). People in all six major religious groups overwhelmingly say they are very free to practice their faiths, and most say that people of other faiths also are very free to practice their own religion.
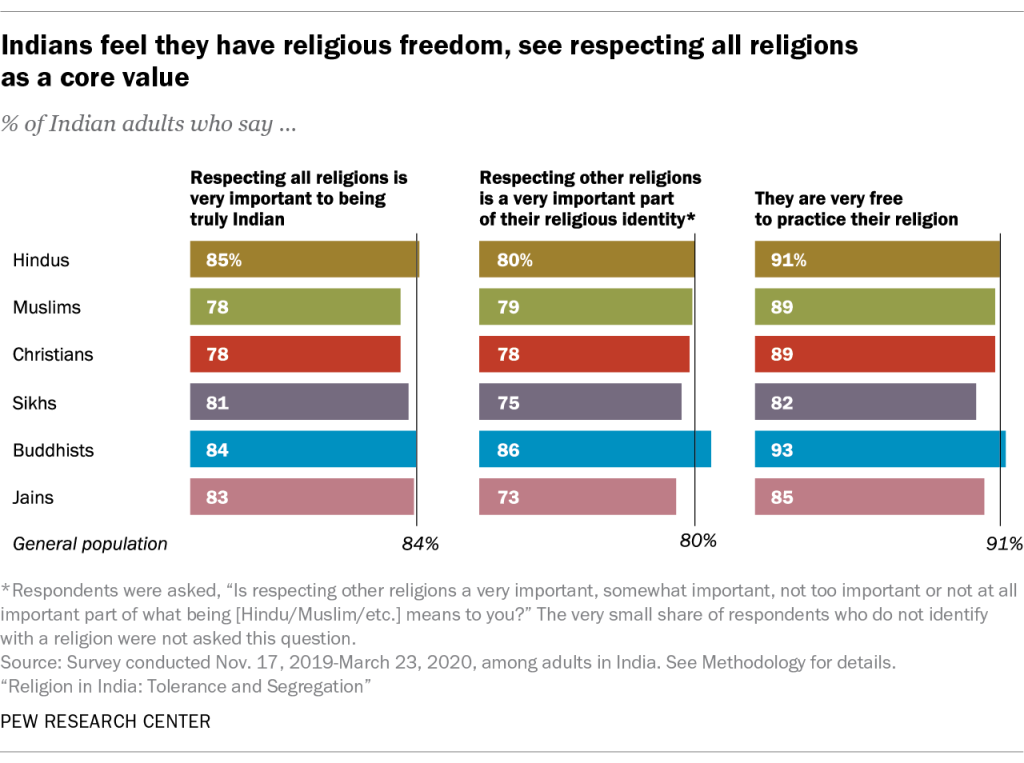
But Indians’ commitment to tolerance is accompanied by a strong preference for keeping religious communities segregated. For example, Indians generally say they do not have much in common with members of other religious groups, and large majorities in the six major groups say their close friends come mainly or entirely from their own religious community. That’s true not only for 86% of India’s large Hindu population, but also for smaller groups such as Sikhs (80%) and Jains (72%).
Moreover, roughly two-thirds of Hindus say it is very important to stop Hindu women (67%) or Hindu men (65%) from marrying into other religious communities. Even larger shares of Muslims oppose interreligious marriage: 80% say it is very important to stop Muslim women from marrying outside their religion, and 76% say it is very important to stop Muslim men from doing so.
2. For many Hindus, national identity, religion and language are closely connected.
Nearly two-thirds of Hindus (64%) say it is very important to be Hindu to be truly Indian. Among Hindus who say it is very important to be Hindu to be truly Indian, 80% also say it is very important to speak Hindi to be truly Indian.
Most Hindus in India say being Hindu, being able to speak Hindi are very important to be ‘truly’ Indian
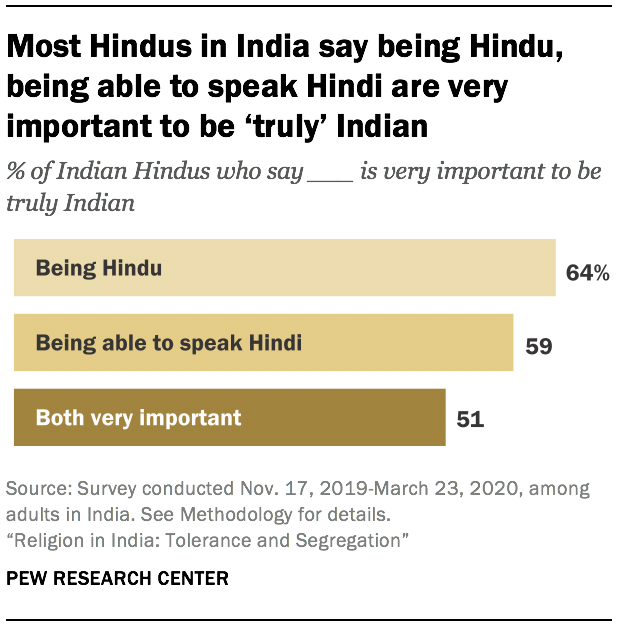
Hindus who strongly link Hindu and Indian identities express a keen desire for religious segregation. For instance, 76% of Hindus who say being Hindu is very important to being truly Indian feel it is very important to stop Hindu women from marrying into another religion. By comparison, 52% of Hindus who place less importance on Hinduism’s role in Indian identity hold this view about religious intermarriage.
Moreover, Hindus in the Northern (69%) and Central (83%) parts of the country are much more likely than those in the South (42%) to strongly link Hindu identity with national identity. Together, the Northern and Central regions cover the country’s “Hindi belt,” where Hindi, one of dozens of languages spoken in India, is most prevalent. The vast majority of Hindus in these regions strongly link Indian identity with being able to speak Hindi.
3. Among Hindus, views of national identity go hand-in-hand with politics.
Support for the ruling Bharatiya Janata Party (BJP) is greater among Hindus who closely associate their religious identity and the Hindi language with being truly Indian. In the 2019 national elections, 60% of Hindu voters who think it is very important to be Hindu and to speak Hindi to be truly Indian cast their vote for the BJP, compared with 33% among Hindu voters who feel less strongly about both these aspects of national identity. These views also map onto regional support for the BJP, which tends to be much higher in the Northern and Central parts of the country than in the South.
4. Dietary laws are central to Indians’ religious identity.
Hindus traditionally view cows as sacred, and laws on cow slaughter have recently been a flashpoint in India. Nearly three-quarters of Hindus (72%) in India say a person cannot be Hindu if they eat beef. That is larger than the shares of Hindus who say a person cannot be Hindu if they do not believe in God (49%) or never go to a temple (48%).
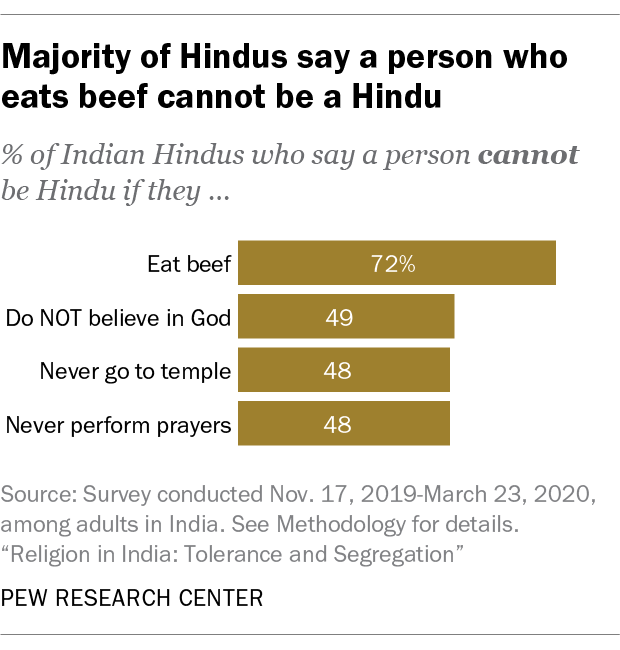
Similarly, three-quarters of Indian Muslims (77%) say that a person cannot be Muslim if they eat pork, which is greater than the share who say a person cannot be Muslim if they do not believe in God (60%) or never attend mosque (61%).
5. Muslims favor having access to their own religious courts.
Since 1937, India’s Muslims have had the option of resolving family and inheritance-related cases in officially recognized Islamic courts, known as dar-ul-qaza. These courts are overseen by religious magistrates known as qazi and operate under Shariah principles, although their decisions are not legally binding.
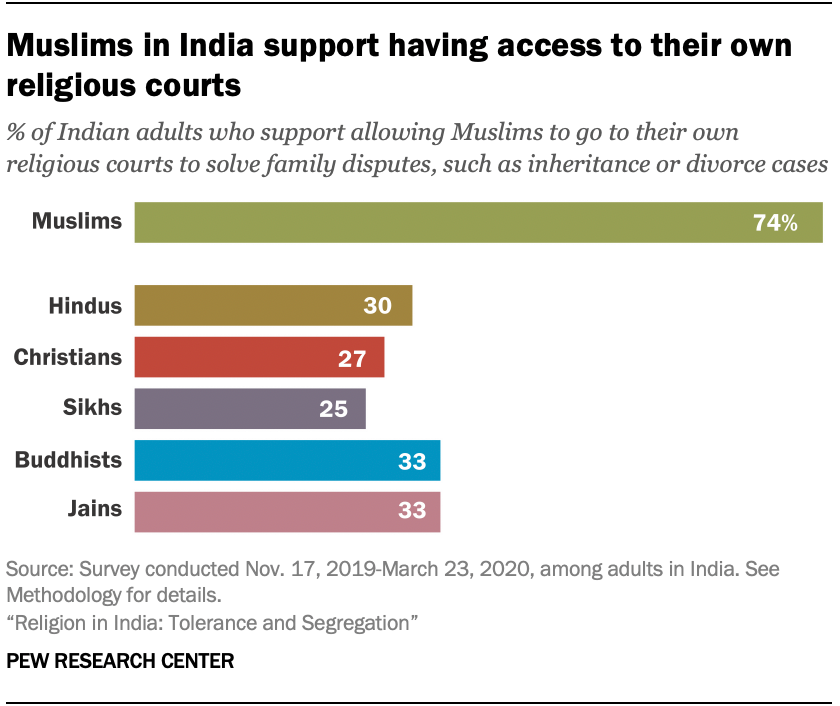
Whether or not Muslims should be allowed to go to their own religious courts remains a hotly debated topic. The survey finds that three-quarters of Muslims (74%) support having access to the existing system of Islamic courts, but followers of other religions are far less likely to support Muslim access to this separate court system.
6. Muslims are more likely than Hindus to say the 1947 partition establishing the separate states of India and Pakistan harmed Hindu-Muslim relations.
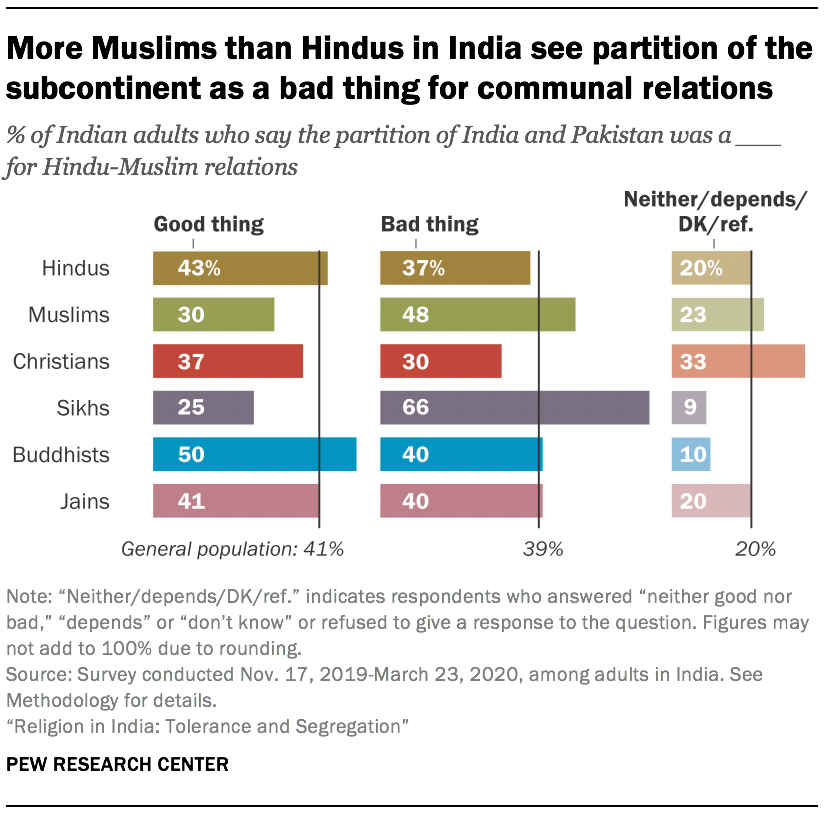
More than seven decades after the Indian subcontinent was divided into Hindu-majority India and Muslim-majority Pakistan at the end of British colonial rule, the predominant view among Indian Muslims is that the partition of the subcontinent was a bad thing for Hindu-Muslim relations (48%). Only three-in-ten Muslims say it was a good thing.
Hindus, however, lean in the opposite direction: 43% of Hindus say Partition was beneficial for Hindu-Muslim relations, while 37% say it was harmful. Sikhs, whose historical homeland of Punjab was split by Partition, are even more likely than Muslims to say the event was bad for Hindu-Muslim relations: Two-thirds of Sikhs (66%) take this position.
7. India’s caste system, an ancient social hierarchy with origins in Hindu writings, continues to fracture society.
Regardless of whether they are Hindu, Muslim, Christian, Sikh, Buddhist or Jain, Indians nearly universally identify with a caste. Members of lower caste groups historically have faced discrimination and unequal economic opportunities, but the survey finds that most people – including most members of lower castes – say there is not a lot of caste discrimination in India. The Indian Constitution prohibits caste-based discrimination, including untouchability, and in recent decades the government has enacted economic advancement policies like reserved seats in universities and government jobs for members of some lower-caste communities.
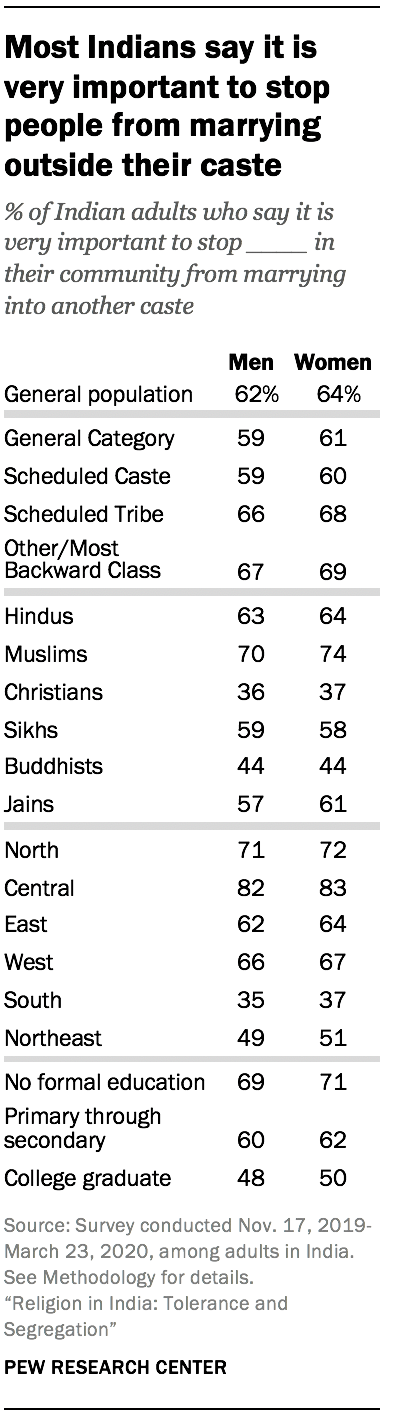
Still, a large majority of Indians overall (70%) say that most or all of their close friends share their caste. Much as they object to interreligious marriages, a large share of Indians (64%) say it is very important to stop women in their community from marrying into other castes, and about the same share (62%) say it is very important to stop men in their community from marrying into other castes. These figures vary only modestly across different castes.
8. Religious conversion is rare in India; to the extent that it is occurring, Hindus gain as many people as they lose.
Conversion of people belonging to lower castes away from Hinduism to other religions, especially Christianity, has been contentious in India, and some states have laws against proselytism. This survey, though, finds that religious switching has a minimal impact on the size of religious groups. Across India, 98% of survey respondents give the same answer when asked to identify their current religion and, separately, their childhood religion.
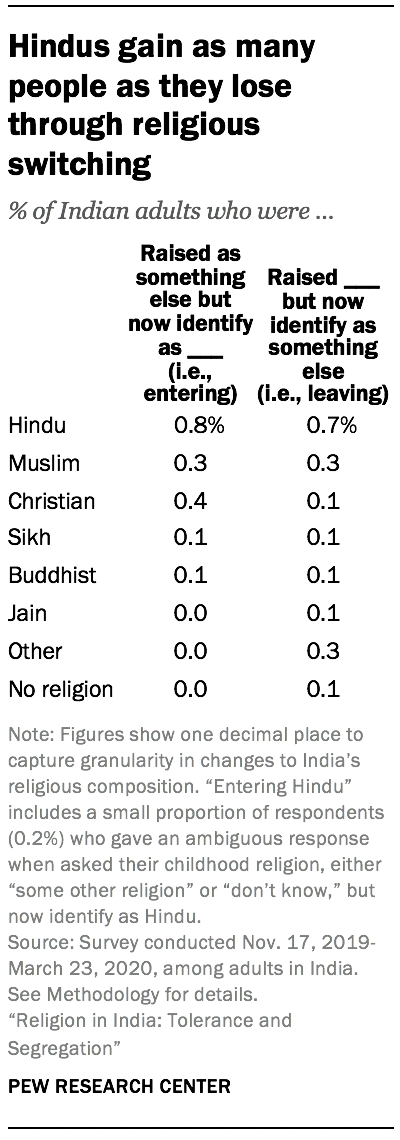
An overall pattern of stability in the share of religious groups is accompanied by little net change from movement into, or out of, most religious groups. Among Hindus, for instance, any conversion out of the group is matched by conversion into the group: 0.7% of respondents say they were raised Hindu but now identify as something else, and roughly the same share (0.8%) say they were not raised Hindu but now identify as Hindu. For Christians, however, there are some net gains from conversion: 0.4% of survey respondents are former Hindus who now identify as Christian, while 0.1% were raised Christian but have since left Christianity.
 Brigadier General Wais Waheed, Commandant of Maldives the Marine Corps, seeks Indian help to enchance Maldives defence capabilities (Image:PIB, MNDF)
Brigadier General Wais Waheed, Commandant of Maldives the Marine Corps, seeks Indian help to enchance Maldives defence capabilities (Image:PIB, MNDF)



 Sikh devotees light candles at the Golden Temple in Amritsar, India, on June 25, 2021. (Narinder Nanu/AFP via Getty Images)
Sikh devotees light candles at the Golden Temple in Amritsar, India, on June 25, 2021. (Narinder Nanu/AFP via Getty Images)







Thank you.