Let me make sure I understand everything correctly. You have an OpenWRT router which terminates a Wireguard tunnel, which your phone will connect to from somewhere on the Internet. When the Wireguard tunnel lands within the router in the new subnet 192.168.2 0/24, you have iptable rules that will:
- Reject all packets on the INPUT chain (from subnet to OpenWRT)
- Reject all packets on the OUTPUT chain (from OpenWRT to subnet)
- Route packets from phone to service on TCP port 8080, on the FORWARD chain
- Allow established connections, on the FORWARD chain
- Reject all other packets on the FORWARD chain
So far, this seems alright. But where does the service run? Is it on your LAN subnet or the isolated 192.168.2.0/24 subnet? The diagram you included suggests that the service runs on an existing machine on your LAN, so that would imply that the router must also do address translation from the isolated subnet to your LAN subnet.
That's doable, but ideally the service would be homed onto the isolated subnet. But perhaps I misunderstood part of the configuration.
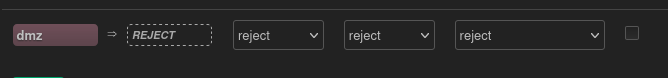 wg1 is in zone dmz
wg1 is in zone dmz
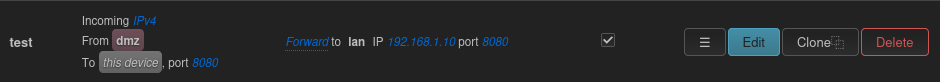 this is the port forward
this is the port forward