this post was submitted on 01 Aug 2023
90 points (96.9% liked)
[Dormant] moved to !space@mander.xyz
10767 readers
1 users here now
This community is dormant, please find us at !space@mander.xyz
You can find the original sidebar contents below:
Rules
- Be respectful and inclusive.
- No harassment, hate speech, or trolling.
- Engage in constructive discussions.
- Share relevant content.
- Follow guidelines and moderators' instructions.
- Use appropriate language and tone.
- Report violations.
- Foster a continuous learning environment.
Picture of the Day
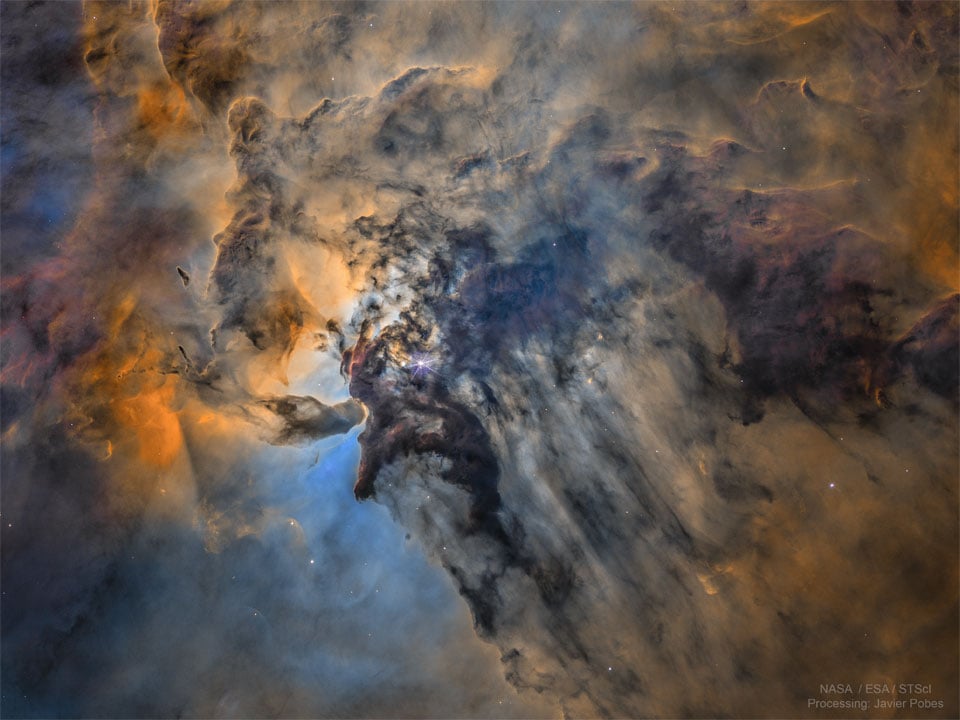 The Busy Center of the Lagoon Nebula
The Busy Center of the Lagoon Nebula
Related Communities
🔭 Science
- !astronomy@mander.xyz
- !curiosityrover@lemmy.world
- !earthscience@mander.xyz
- !esa@feddit.nl
- !nasa@lemmy.world
- !perseverancerover@lemmy.world
- !physics@mander.xyz
- !space@beehaw.org
- !space@lemmy.world
🚀 Engineering
🌌 Art and Photography
Other Cool Links
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
That is horrifying. Windows Server 2003 is 8 years past EOL meaning it hasn’t received any security patches since then. For such a highly regulated industry your entire tech department need’s launched into the sun.
Microsoft Lifecycle Documentation
I work in the tech department for a company and I guarantee that they have made management aware and management's response was "No it costs money, so I don't want to. Anyway it's working fine."
It's our job to tell management that they're being idiots, but it really is their responsibility to stop being idiots. If they don't, that's on them, and I have the emails to prove it.
Modern ransomware probably wouldn't run on those old systems anyway haha
Well big businesses can pay Microsoft past the EOL to maintain patches if it's worth it for them. Doubt many do though LOL